Prerequisites
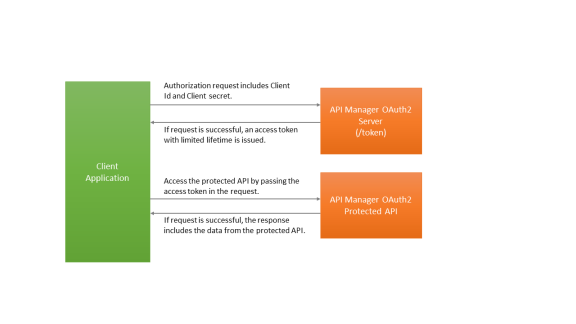
Register an application with the API Manager and subscribe to at least one API that is protected using OAuth2. Also, specify a callback URL (or redirection URL) with the API Manager application so that after authorization request is completed user is redirected to this registered URL. The registered application includes Client ID and Client Secret, which are required for this flow/grant type.
Requesting an access token
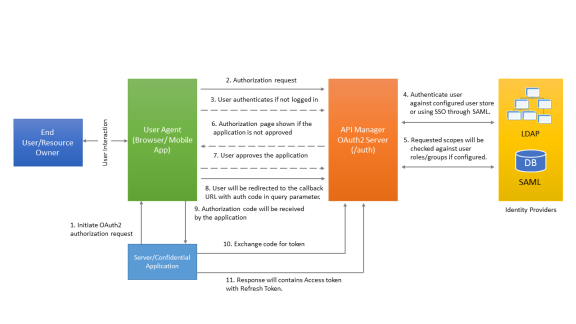
The flow begins by the application server component redirecting the end user to API Manager OAuth2 server authorization endpoint (/oauth2/auth). The URL for sending the authorization request is shown below:
http://<APIM_SERVERNAME>:port/oauth2/auth?client_id=<Application Client ID>&response_type=code&scope=<list of scopes delimited by string>&state=<random string>
An example URL is:
http://example.com/oauth2/auth?client_id=9a42a56d5b5546079f2f82a62612dab9&response_type=code&
state=nkj34898sdcsd123&scope=foo_read%20foo_write
Request Parameter
|
Description of the parameter
|
response_type
|
The parameter identifies the flow of the grant type. The value is code.
|
client_id
|
The Client Id of the application which uniquely identifies the application. The client id can be found in the API Manager application.
|
state
|
An opaque pseudo- random string value used by the client application to maintain state between the initial authorization request and callback. The parameter is used to prevent cross-site request forgery. Store the state in a server-side session for comparing it later.
|
scope (optional)
|
Specifies the list of scopes required for the access token. If multiple scopes are required, specify the scopes as a space delimited string.
|
Once the API Manager OAuth2 server receives this request, it validates all the parameters. If the parameters are valid, the user sees a login page where the user is asked to provide the login credentials (user name and password). If the authentication method for the application is SAML SSO, the user is redirected to the SAML Identity provider for authentication.
After the authentication is successful, you are presented with another page where you can provide the authorization/consent. Here you can select the list of scopes that are permitted for the application, which in turn is provided to the access token. Once scopes are selected and approved, you are redirected (to the registered URL) back to the application. You attach a query parameter called code with its value along with the state parameter.
Now the application server component verifies the state parameter value received from the request with the value stored in the session. If state parameter is verified, then extract the code parameter value from the request and use client credentials to redeem this code for an access token.
POST example.com/oauth2/token HTTP/1.1
Host: server.example.com
Content-Type: application/x-www-form-urlencoded
grant_type=authorization_code&client_id=9a42a56d5b5546079f2f82a62612dab9&
client_secret=7ee85874dde4c7235b6c3afc82e3fb
If the given client credentials & the authorization code are valid the response will contain an access token along with a refresh token. Refresh token is used to get a new access token when the current access token is expired/revoked. The JSON response includes the following keys.
A sample JSON response is shown below.
{
"access_token": "95d9c3de53a9c48e629ecb6a288f6c",
"token_type": "bearer",
"expires_in": 1200,
"scope": "foo_read",
"refresh_token": "31cf059933238e866779a43237cd7ec"
}
JSON Key
|
Description of the Key
|
access_token
|
The requested access token which can be used to call the protected API.
|
token_type
|
Specifies the type of the requested access token. Currently API Manager supports bearer tokens only so the value is Bearer.
|
expires_in
|
The lifetime in seconds of the access token. The access token lifetime can be configured by changing the access token lifetime in API Manager application.
|
client_id
|
Client Id of the application for which the access token is issued.
|
State
|
An opaque pseudo- random string value used by the client application to maintain state between the initial authorization request and callback. The parameter is used to prevent cross-site request forgery.
|
scope
|
The Granted/Approved scopes associated with the requested access token.
|
refresh_token
|
Refresh token is a long-lived access token which is used to ask for a new access token.
|
To retrieve this information any time, the client application can pass the requested access token to the token info endpoint. Once the issued access token expires, the application can use the refresh token to get a new access token.
Refreshing access token
The example below shows how to refresh an access token using refresh token. Pass the client credentials along with the request, either through form parameters or using basic authentication.
POST example.com/oauth2/token HTTP/1.1
Host: server.example.com
Authorization: Basic czZCaGRSa3F0MzpnWDFmQmF0M2JW
Content-Type: application/x-www-form-urlencoded
grant_type=refresh_token&refresh_token=31cf059933238e866779a43237cd7ec&scope=foo_read
If the refresh token is expired/revoked, the application starts the three-legged dance once again. In case of user store authentication, if the authentication times out, provide valid credentials (user name and password) again to log in. In case of SAML SSO IDP, authorization happens again. If the application is already approved, you are redirected to the callback URL immediately with the intermediary authorization code and state.
Access/refresh token revocation
Each issued access token has an associated expiry time. Once the expiry time is reached, the access token becomes invalid & revoked automatically. Once the access token expires, the application gets a new access token. If the access token has to be revoked before its expiry time, pass the access token to the revocation endpoint.
The access token revocation request is sent to the API Manager OAuth2 revocation endpoint. The following sample HTTP request revokes the access token:
POST example.com/oauth2/revoke HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
token=7ee85874dde4c7235b6c3afc82e3fb&token_type_hint=access_token
The revoke endpoint also supports revoking the refresh token pass the refresh token in token parameter and set token_type_hint parameter value as refresh_token.
Security considerations
The security of OAuth2 depends on the secure transmission of user credentials, OAuth2 access tokens, and client credentials. Therefore, accessing all the OAuth2 endpoints on HTTPS (SSL/TLS) transport is recommended for production environments. The API Manager administrator can mandate HTTPS transport only in the Security Configuration page. Also, HTTPS URL callback is registered with the API Manager application because the callback URL receives the authorization code. The server application verifies the state parameter value received in the request with the value stored in the session. The server application securely stores the access tokens, refresh tokens, and client credentials in a secure database.